-
- file_download
-
2 个项目 147.22 KB
README
Easy Rev
Description
Reverse Easy.....
Solution
First we execute the binary
$ ./baby_re_2
Looking for the flag?
Enter the key: test
Wrong! Try Again ...We try to analyze a binary to find the key using ghidra. We look up FUN_00101277 function and we see some interest.
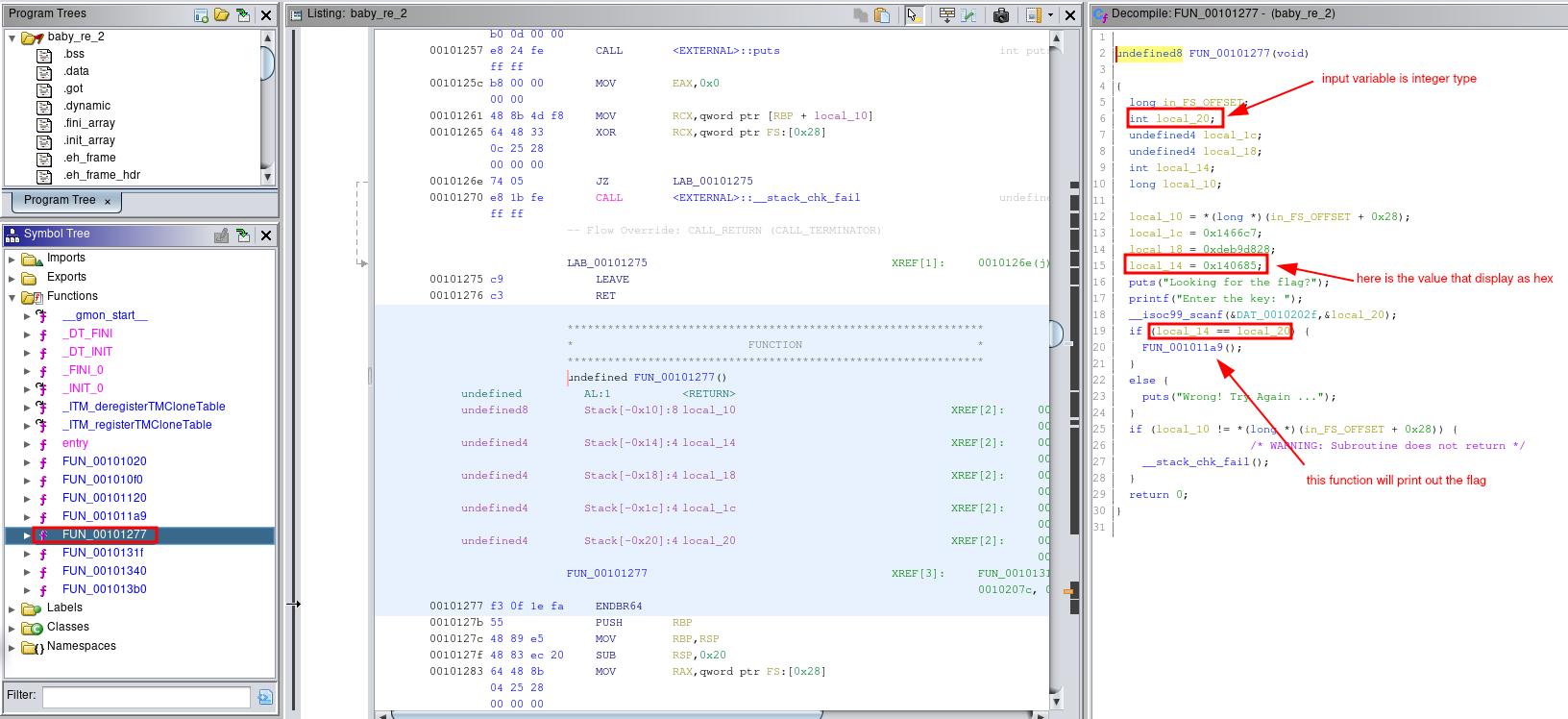 First we look at
First we look at line 19 we show a condition that will execute another function. And we see local_20 is an input variable and local_14 variable that equal = 0x140685(Hex). Since the integer variable is readed as decimal so we try to convert the value of local_14 to Decimal.
140685 (Hex) = 1312389 (Decimal)
So we found the key and we try to execute again
$ ./baby_re_2
Looking for the flag?
Enter the key: 1312389
GrabCON{y0u_g0t_it_8bb31}We got flag!